In today’s cybersecurity landscape, protecting sensitive informationSensitive information is a broad term that encompasses any d... More is more critical than ever. The latest “Cyber Security in Focus report” by Stott and May shows that 22% of CISOs rank data protection as the highest priority, only behind Cloud Security at 29%. With such a huge focus, vendors are looking for the hottest new category or craze to wrap their marketing dance moves around. One of those hyped and potentially misused terms is Data Detection and Response. But is it really the Data Dance Revolution it claims to be, or just a new step in a familiar routine?
Similar to one of my first ever blogs at Symmetry on the origin and meaning behind data security posture management, I did some research into where DDR originated and how it is being used, before comparing it to preexisting data security categories.
What is Data Detection and Response (DDR), and Where Did It Come From?
Data Detection and Response (DDR) is the newest addition to the (insert letter)DR family of security acronyms. It builds upon the popularity of EDR and XDR as hugely successful market categories. DDR shifts the focus from endpoints directly to safeguarding data where it lives, aiming to prevent data breaches by:
- Detecting threats targeting data at rest, in motion, or in use;
- Proactively reducing exposures to the data that could be exploited by these threats; and
- Responding quickly to these threats as part of a comprehensive cybersecurity incident response process.
In practice, DDR is used by marketing teams to describe any product or services that offers a combination of 1 or more of these capabilities.
It’s hard to pin down exactly when people first started using the term “Data Detection and Response.” However, we do know that one of the first times it showed up online was in September 2022 by a next generation DLP vendor as well as an emerging DSPM vendor. Fast forward to today, a raft of Data Security Posture Management and Cloud Security vendors have adopted the term as an extra capability on top of existing capabilities.
In general this nuanced positioning continues with either:
- DDR as Advanced DLP: This approach positions DDR as an evolution of traditional DLP, with enhanced real-time capabilities and more sophisticated detection and response mechanisms for data-centric threats. This represents a more right of boom focus where Incident response is the key focus.
- DDR as Actionable DSPM: This perspective presents DDR as an add-on to DSPM with added real-time response features, bridging the gap between posture management and active threat mitigation. This represents a more left of boom focus where Risk reduction is the key focus.
So Is It Just DLP 2.0 or DSPM with Better Outcomes?
As the hype around data security continues to evolve, there is growing skepticism about whether DDR is truly a separate category or just a reinvention of Data Leakage Prevention or extension of Data Security Posture Management (DSPM) with automated remediation.
For example, Anton Chuvakin believes, as outlined in his blog post “What ?DR or What Detection Domain Needs Its Own Tools?“, that DDR probably shouldn’t exist as a separate category. His rationale being that it is not really a distinct technology domain. The always insightful Chuvakin argues that existing tools have long been used for visibility into external data flows and, despite some limitations, ultimately deliver on data movement detection, investigation, and response. Therefore, DDR’s functions are largely covered by the existing technology and don’t warrant a new, separate category of tools.
Capability Comparisons: DDR vs. Existing Security Categories
So here’s the question: Does DDR truly represent a separate category or if it’s simply a reinvention of existing solutions. Let’s compare the broad capabilities of DDR to some established security approaches:
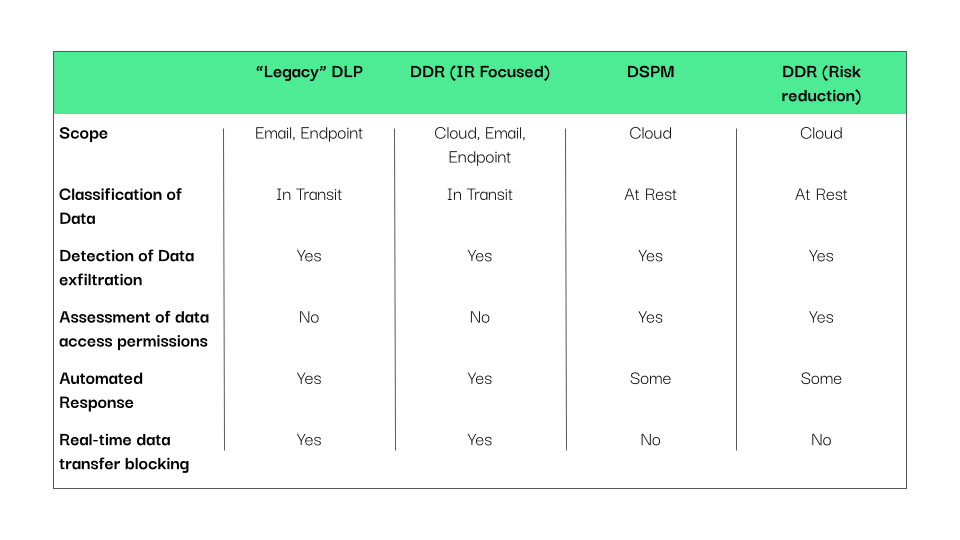
As we’ve seen, the use of DDR has sparked some debate over its legitimacy as a standalone category. While DDR brings new terminology to the security conversation, it’s important to recognize that the capabilities it touts are not entirely novel. Whether it’s a more refined form of DLP or an enhanced DSPM with real-time actions, DDR overlaps heavily with existing technologies that have been securing data for years.
The comparison table above highlights that many of DDR’s features can be found in tools we’ve long been familiar with—whether it’s legacy DLP’s exfiltration prevention or DSPM’s nuanced access controls and risk reduction strategies. And while DDR expands certain real-time responses to new scopes that make it feel fresh, one has to ask: is that enough to justify carving out an entirely new product category?
The larger issue may lie in the security market’s tendency to repackage and relabel. Buzzwords often mask a fundamental truth: DDR is a natural progression of what’s already being done in DLP, DSPM, and other security strategies. In other words, it’s another iteration in the ongoing evolution of data security, not a groundbreaking revolution.
DDR: A Familiar Dance in New Shoes?
The key to understanding DDR is realizing that it doesn’t introduce a new security philosophy or framework. Instead, it extends the capabilities of existing tools, adding some real-time elements and automated responses. For organizations exploring DDR, the question isn’t whether it replaces traditional DLP or DSPM, but whether it enhances them in meaningful ways.
Ultimately, vendors may be performing a new dance with DDR, but it’s a routine that security teams already know well. And as always, the focus should remain on outcomes—how effectively the tool in question protects sensitive data. After all, no matter what new acronym or buzzword gets thrown around, the goal remains the same: keeping data safe from evolving threats.
DDR may not be the “data dance revolution” it’s billed as, but it can still play a useful role in the broader cybersecurity choreography—just don’t expect it to steal the show.



