At Symmetry, our mission has always been to safeguard the world’s data. We realize that with this lofty mission, we can’t do this alone. Traditional Data LossData loss refers to the accidental or unintentional deletion... More Prevention (DLPDLP, or Data Loss Prevention (also known as Data Leak Preven... More) solutions have a strong focus on the network, endpoints and email. As a result, they have been effective in reducing preventable data breaches and unauthorized data exposure through these vectors and will remain so. We don’t think DLP is dying, unlike the bold claim by Avivah Litan many years ago. However, system architecture and the digital economy is evolving, and so has the approach to data protectionData protection refers to the set of laws, regulations, and ... More and to DLP.
The concept of “shifting left” was popularized in the software development world. It is similarly doing so in DLP practices. Cloud architectures, the gravitational pull of data and the proliferation of APIs drives DLP practices left – closer to the data. These factors combine to keep data within the new cloud perimeter by enabling secure, seamless data integration across enterprise ecosystems. This blog explores why DLP has moved closer to data stores and how this shift is transforming data security strategies.
What is “Shift Left”?
The term “shift left” has been widely adopted in both software development and cybersecurityCybersecurity refers to the practice of protecting systems, ... More, promoting the integration of quality and security practices earlier in the lifecycle of projects. The roots of the term were focused on “shift left testing” . This can be traced back to a paper by Larry Smith in 2001. Smith’s advocacy for moving testing earlier in the software development lifecycle (SDLC) marked a departure from traditional models, most notably the waterfall method. The waterfall method is a sequential development approach, where testing was relegated to the final phases of development. This late-stage testing often resulted in costly and time-consuming fixes for issues that could have been identified and mitigated much earlier.
Shift left testing, and the broader shift left approach, emerged as solutions to these inefficiencies, advocating for the early and frequent integration of testing throughout the SDLC. Similarly the shifting left of data protection can address data loss issues much earlier in the data’s life cycle.
What is Forcing DLP to Shift Left?
The playbook for keeping data safe is being rewritten by broader trends across the industry. It’s not just about slapping on a Band-Aid right after an alert is generated to prevent it from happening again, or warning someone that what they are doing might be bad. It’s about building paved roads, with guardrails, and seat belts to keep the data where it belongs. And in the modern data stack, data no longer belongs in email, endpoints, or being uploaded by end users.
You should rethink your DLP strategy, if it is solely focused on watching over endpoints, scanning emails, or monitoringMonitoring in cybersecurity involves continuously observing ... More network flows like a hawk. Modern organizations interact with data almost exclusively in the cloud. And will do increasingly more, given the impact of data gravity, the ubiquity of cloud computing, and the rise of API driven architectures. In a modern organization, data is the center of the solar system, pulling applications, services, and more data into its orbit with data gravity. APIs act as the express lanes for data movement between applications, and third parties, facilitated by the identities with access. Let’s unpack how these factors are guiding us towards a future where data security is more intrinsic and woven into the fabric of how data is created, shared, and stored.
Cloud First Architecture
Cloud computing has taken center stage, while traditional DLP strategies have remained centered on endpoints, as well as the email and network flows from the endpoint or end user. The shift requires recognizing the “identity perimeter” in cloud environments, where data security hinges on who has access, controlling where it can flow outside of the trusted environment. The move reflects a need for deeper integration of DLP measures with the cloud’s fabric, emphasizing the need to secure data based on identities and access rights in the cloud and data stores.
Data Gravity
Data gravity, a concept that describes how data attracts applications, services, and other data, is also a significant force behind the shift in DLP strategies. As more data accumulates in centralized locations (such as cloud data stores), the gravity increases, drawing in more applications and services that aim to leverage this data without the need to extract the data and replicate the data somewhere else. This reduces the unnecessary flow of data outside the trusted cloud environments. This centralization of data necessitates a reevaluation of traditional perimeter-based security models, which are less effective in a landscape where data is the central axis around which business operations revolve.
Rise of APIs
Similarly the rise of Application Programming Interfaces (APIs) revolutionizes how data is accessed, manipulated, and shared across different applications and platforms. Users no longer need to download the data to csv, so they can manipulate the data on their desktop. APIs facilitate the secure and efficient integration of data into various enterprise use cases, reducing the reliance on traditional methods of data movement and manipulation, such as email transmissions, network uploads, and exports to desktop applications. This ease of integration and sharing underscores the need for a data-centric approach to DLP, where the focus is on protecting the data at its source rather than just monitoring its movement.
Where is it shifting to?
Diving into this shift-left philosophy means organizations have to gear up with modern tools that are up for the challenge, and that’s where Data Security Posture ManagementData Security Posture Management (DSPM) is an emerging cyber... More (DSPMA term originally coined by Gartner, data security posture ... More) comes into play. Think of DSPM as the ultimate construction crew for your data security highway. It’s about laying down smooth, paved roads, installing sturdy guardrails, and making sure everyone’s buckled in with seat belts. Why worry so much about what is being sent via email, or saved on endpoints? DSPM gives organizations the blueprint and the tools to keep their data securely on the right path, constantly monitored and managed to prevent any mishaps. For those ready to embrace the shift-left mindset, bringing DSPM into their toolkit means they’re not just reacting to threats but actively designing a safer, more secure environment for their data to thrive in.
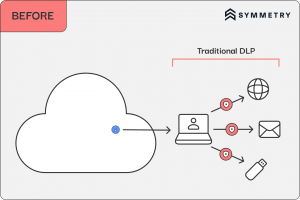
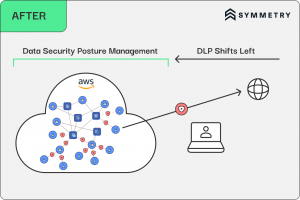
The Benefits of Shifting DLP Left
By emphasizing the integration of data security closer to the data sources or data stores, rather than as a perimeter afterthought, organizations can enhance their security posture in a more comprehensive and effective manner. The benefits of adopting this forward-thinking approach are manifold, addressing both the immediacy of unauthorized access to data and enforcing the efficacy of zero trustZero Trust is a security concept that businesses deploy to s... More architecture.
Proactive Rather Than Reactive
By focusing on the data stores themselves, organizations can adopt a more proactive stance in their security measures. This involves classifying, encrypting, and controlling access to data at its source, significantly reducing the risk of unauthorized access or data breaches much later – often too late.
DLP becomes about more than Confidentiality
Taking a step back, the idea of shifting DLP left isn’t just about preventing data leaks anymore. It’s a data security game changer that brings the whole package – making sure data is not just confidential but also there when you need it and in the right shape. Think of it as hitting the trifecta in data security: keep things under wraps (confidentialityConfidentiality is the principle of ensuring that informatio... More), make sure the data shows up for work every day (availabilityAvailability is a key aspect of information security, ensuri... More), and ensure it hasn’t gone rogue or been tampered with (integrityIn the context of data security and privacy, integrity refer... More). Companies can tackle the whole spectrum of data risks head-on by weaving security into how data is handled right from the get-go.
Embracing a Zero Trust Architecture
The principles of Zero Trust architecture operate on the assumption that threats can originate from anywhere, and therefore, nothing should be trusted implicitly. Shifting left with DLP aligns with these principles, as authorization and authenticationAuthentication is the process of verifying and confirming th... More controls aren’t easily enforceable when data leaves the modern data stack to an endpoint or user’s email systems. Zero Trust necessitates robust authentication, authorization, and encryptionEncryption is the process of converting plaintext data into ... More practices directly at the data layer, ensuring that data security does not solely rely on network or endpoint securityEndpoint security involves protecting devices such as comput... More.
Conclusion
The shift left in DLP strategies marks a significant evolution in the approach to data security. Driven by the undeniable forces of data gravity and the rise of APIs, organizations are now recognizing the need to protect data at its source. This paradigm shift from perimeter-based security to a data-centric model is not just a strategic move but a necessity in today’s data-driven world. As we move forward, the integration of advanced DLP solutions at the data storeA data store is a repository or storage system used for stor... More level will become a cornerstone of robust data protection strategies, ensuring that sensitive informationSensitive information is a broad term that encompasses any d... More remains secure in an increasingly interconnected ecosystem.



