There is no denying that businesses are under increasing pressure to fortify their defenses and better protect sensitive information. Ransomware payments in 2023 surpassed the $1 billion mark, and don’t show any sign of slowing down. Since December 2022, Microsoft observed a “doubling of potential data exfiltration instances after threat actors compromised an environment”. The counterpoint to these awful statistics is the emergence of data security posture management, which involves the continuous assessment, monitoring, and enhancement of an organization’s data security.
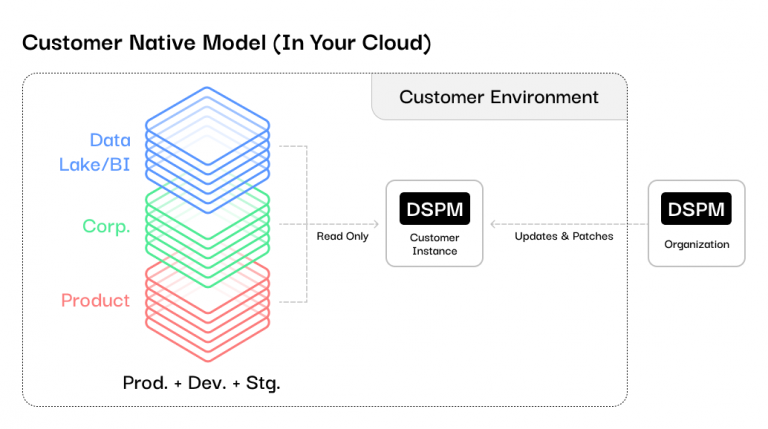
What is Customer Native DSPM? Customer Native DSPM refers to a data security approach where the DSPM solution is deployed and operates solely within the customer’s own cloud or on-premise environment and infrastructure, rather than from being delivered as an external service. Also referred to as an In-Your-Cloud deployment.
However, while some DSPM providers advocate traditional Software as a Service (SaaS) or an outpost model, there is a compelling argument for conducting data security posture management completely from within the customer’s environment (customer-native).
Symmetry supports all three of these models based on customer needs, but increasingly finds customers wanting Customer Native deployment. Here’s why:
Maintain Full Data Control and Custody
The age old security adage that you can’t protect what you can’t see rings true in DSPM. Maintaining visibility and control over sensitive data is paramount for effective data security. Crucially, by operating within the customer’s environment, sensitive data like intellectual property, financial records, and PII never leaves trusted infrastructure.
It remains governed by the organization’s established security policies, controls, and guardrails. This includes best practices leveraging AWS Service Control Policies, Azure Management Groups, or Google Cloud’s Organization Policy Service. This eliminates the risks associated with routing sensitive data outside the customer’s policy control plane. Ensuring comprehensive, real-time oversight and custody of their most valuable data assets.
Reduce Third-Party Security and Compliance Risk
For highly regulated industries like finance, healthcare, and government, outsourcing critical functions like security introduces significant compliance risks and complex oversight obligations. Stringent regulations from bodies like APRA, FCA, MAS, FINMA, and IOSCO mandate that regulated entities are rigorous in their management of risk of outsourced material functions and critical data.
By deploying DSPM capabilities entirely within their cloud environments, organizations avoid most of these outsourcing implications altogether. There is no external data shared with a third-party or reliance on the third party infrastructure to perform this critical security function. This eliminates the need for complex due diligence, oversight, and control procedures required when leveraging external vendors. More importantly, the vendor operations occur within the secure confines of their own cloud infrastructure, governed by their existing security controls, encryption, audit logging, and compliance certifications. Organizations retain complete ownership and control over all security monitoring data, logs, and metadata.
Avoid Costly Egress Fees
This may be less of a concern than others, unless you haven’t done the appropriate due diligence on the hosting of the DSPM SaaS platform is the avoidance of potentially steep data egress fees from cloud providers. With egress costs ranging from $0.09 to $0.20 per GB transferred out and even between regions, prices can quickly escalate for data-intensive workloads.
External DSPM solutions may need to extract large volumes of data, such as logs, metadata, and configuration details, from the customer’s cloud accounts for monitoring and analysis.
Customers that deploy DSPM within their cloud environment eliminate these egress fees entirely, as all monitoring, detection, and analysis occur within the own trusted virtual private cloud (VPC) network without ever crossing egress boundaries.
Maintain Compliance Boundaries and Leverage Prior Investments
For organizations dealing with highly regulated data (such as PCI or HIPAA) or bound by regulations dictating who you can do business with (such as ITAR, FEDRAMP or CMMC), maintaining compliance with security standards and certifications is a cost of doing and staying in business. Their cloud environments have likely undergone rigorous audits and reviews to achieve compliance certifications.
However, introducing external DSPM solutions that operate outside the compliance boundary can potentially undermine these hard-won compliance postures. Data flows, access controls, auditing, and governance controls now have to extend to cover this third-party.
An in-your-cloud DSPM avoids creating this extended compliance boundary. Since the DSPM runs within the customer’s existing and compliant environment, there’s no need to expand auditing or re-validate controls. The DSPM solution can easily integrate with and extend visibility across their existing controls, processes, logs and other compliance-enforcing architectures.
The Counter Arguments
Like most technology decisions, there is often a counter argument to be made for the alternative approach. This is no different.
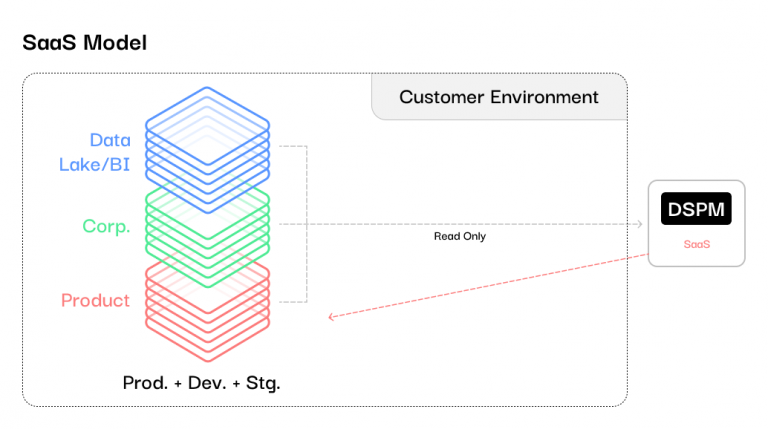
The Convenience of Traditional SaaS DSPM
The convenience of a multi-tenant SaaS model is the biggest counterargument for conducting DSPM within a customer’s cloud environment. With a cloud-hosted service, deploying security capabilities is as simple as enabling an account and feeding data streams. No infrastructure provisioning or software deployments are required, as the vendor takes on the operational burdens of software updates, scalability, and runtime management.
However, this SaaS approach for DSPM reintroduces all the core risks already covered. The limited data custody and control, extended compliance scope, egress fees, and potential for data exposure or residency violations is challenging. For highly regulated industries or environments with sensitive data, the push of data into an opaque, multi-tenant cloud is untenable.
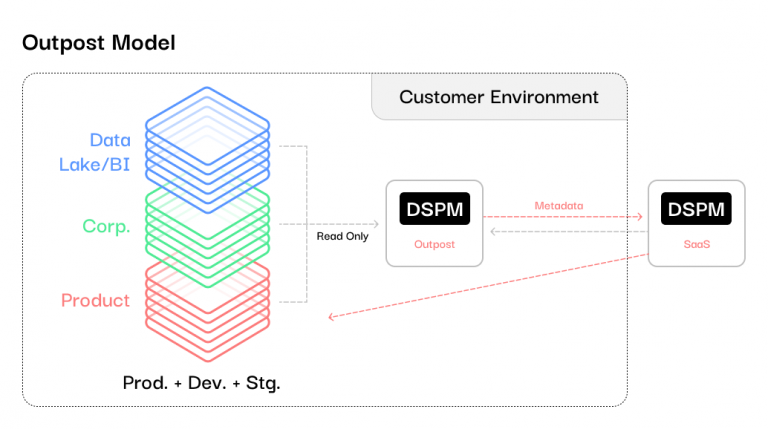
It’s Just MetaData
Some vendors have attempted to strike a middle ground with deployment models that keep sensitive data within the customer environment . These models still however transmit metadata externally for presentation. The argument is that by only sending metadata to the vendor’s systems, the highest risks around data exfiltration are mitigated. The actual regulated data remains behind the customer’s firewalls. However, these bastion or outpost approaches still have significant shortcomings:
-
- Metadata potentially exposes sensitive context that could enable unauthorized access if compromised, violating compliance requirements around data custody. We often see personal information stored in file names or directory structures.
-
- The constrained capabilities of serverless functions typically used in these outpost models means that vendors are only able to provide limited data classification. Sometimes only offering simplistic REGEX.
-
- There are visibility gaps from not having the vendor’s systems able to directly inspect data flows, access patterns, configurations and activities within the customer’s environment in full fidelity. This obscured visibility increases the risk of missing threats.
-
- Lack of deep bi-directional integration with the cloud provider’s native monitoring and security capabilities.
-
- Creates a fragmented security data plane spanning multiple environments, increasing complexity and potential stack blindspots.
So while keeping data storage within the customer environment is a step in the right direction, these hybrid models don’t fully resolve concerns. They inevitably trade off some degree of risk, visibility or integration. At least, compared to a true in-your-cloud deployment where all DSPM operations occur natively within the customer environment
Pioneering In-Your-Cloud DSPM with Symmetry
Symmetry Systems, a pioneer in this field, has revolutionized the way organizations approach DSPM deployments with its customer-native solution. Unlike traditional SaaS deployments, Symmetry recognized the importance of deploying DSPM solutions without compromising data security and control. By creating a customer-native data security platform that can run 100% within a customer’s virtual private cloud (VPC) or private network, Symmetry offers protection and compliance adherence, while still delivering SaaS-like simplicity.
To address historical challenges of deploying data platforms within customer environments, such as lengthy installation procedures, compatibility issues, and data access concerns, Symmetry developed a streamlined deployment process quickly tailored to each customer’s cloud environment. This process is designed to reduce complexity and save time, ensuring a seamless experience for customers. The process is broken down into three phases:
-
- Initial Assessment: Identify the customer’s cloud accounts, log sources, and data stores for deployment.
-
- Setup: Establish a separate cloud account owned by the customer. Deploy Symmetry using Docker images from an approved cloud registry.
-
- Configuration: Create a read only service role using a defined Infrastructure as Code (IAC) template. The role enables Symmetry to query the customer’s cloud accounts, log sources, and data stores.
Once provisioned, they have complete control and custody over their data security posture, with no blind spots. Going forward, Symmetry maintains the operational agility of a cloud service. Symmetry handles all lifecycle management, updates, monitoring and scaling so customers don’t have to staff for it.
By aligning with the Cloud services and production ready, Symmetry ensures that the deployment experience is efficient, controlled by the customer, and fully integrated within their cloud environment. Eliminating the need to choose between security/compliance or convenience.



